IoT devices have become a new trend in Internet active products and they are now being increasingly used everywhere from cars and fridges to assembly lines for automation and monitoring. IoT sensors and devices are expected to exceed 50 billion by 2022, up from an estimated 21 billion in 2018 and the figure is good enough an indication about the staggering rate at which the IoT market is currently growing. While consumer IoT devices are offering lifestyle benefits, businesses are using IoT devices to save cost, monitor important processes, get new insights, increase efficiency and to make informed decisions. For example, Harley-Davidson recorded 7% reduction in costs and 19% increase in net margin after it turned its Pennsylvania plant to a ‘smart factory’ using IoT devices. There’s no denying the fact that IoT devices offer huge benefits, but like other Internet-enabled devices they also do not come without risks. IoT devices risks are real and IoT devices are more vulnerable than other computing devices especially because of increased number of endpoints which expands attack surfaces. Understanding the security vulnerabilities of IoT devices is paramount for you to sufficiently protect your network. Let’s discuss them!
IoT Devices Risks and Vulnerabilities compared to other Computing Devices on a Network
Security Breach Risk because of Lack of Compliance from Manufacturers
Manufacturers release new IoT devices into the market each day but most of them have undiscovered vulnerabilities. One of the major reasons IoT security issues is not spending enough time and resources while manufacturing IoT devices. For example, most fitness trackers that come with bluetooth remain visible after the first pairing. A smart refrigerator can give hackers an opportunity to access gmail credentials. Because of no universal IoT security standard being set as yet, manufacturers tend to create devices with poor security and do not include security as an important element in their product design process. The biggest IoT risks from manufacturing include weak or guessable passwords, unsecured hardware, absence of a secure update mechanism, lack of patching mechanism, insecure data transfer and storage
Security Issues because of No Patching and Update Management
Even if a manufacturer created a secure hardware and software for an IoT product, new vulnerabilities would eventually be discovered. This is the top reason why updates are so important to protect IoT devices from new vulnerabilities. Other devices like computers and smartphones get automatic updates, but some IoT devices lack necessary updates. An important point to consider here is that during an update, a device will be tasked to keep a backup on the cloud causing a short downtime. If encryption technique is not used for the connection and the update files are not protected, a hacker can stand a chance to steal sensitive information. Also, the nature and use of IoT devices make it difficult to release updates regularly. Think of sensors sprawling over hundreds of acres of farmland or of IoT devices on a factory floor that need to go offline for updates resulting in production loss.
Also read 7 factors companies must consider for IoT software app development.
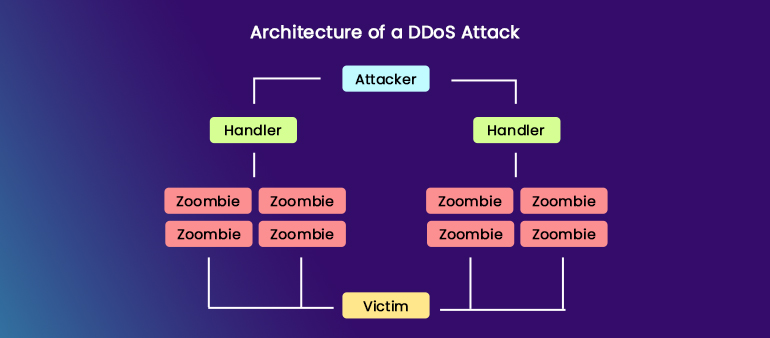
Botnet Attacks
A real threat does not come from just a single IoT device infected with malware, but from many of those infected IoT devices to bring down anything. A hacker can perform a botnet attack by creating an army of bots by using malware and then sending numerous requests per second to bring down targets like electricity grids, transportation systems, water treatment facilities, and manufacturing plants and more. Serious concerns over IoT security were raised after the Mirai bot attack in 2016. A massive distributed denial of service (DDoS) attack brought down the DNS that provided services to platforms like GitHub, Twitter, Reddit, Netflix, and Airbnb. IoT devices can easily fall prey to malware attacks majorly because of no regular software security updates that a computer usually gets. So, IoT devices can be easily turned into infected zombies and can be used to send incredibly vast amounts of traffic.
Lack of Physical Security
Lack of physical hardening can also lead to security breaches. Many IoT devices do not require human intervention but these devices are sometimes installed in remote locations which makes them prone to outer threats. Criminals can physically temper them, for example, by using a USB flash drive with malware. Users must take the responsibility of physically securing their IoT devices. Without adequate protection, a smart motion sensor or a video camera outside a building or house can be tampered with and render any data it collects or relays, unreliable.
Also read how Blockchain and IoT Technology empower each other.
Lack of User Knowledge and Awareness Around IoT
Internet users have learned over the years how to avoid phishing emails, run virus scans on their PCs, and create strong passwords to secure their WiFi networks. But things are not the same with IoT as it’s still a new technology and even many seasoned IT professionals have lack of knowledge and awareness of IoT devices. The 2010 Stuxnet attack against a nuclear facility in Iran strongly shows how the user’s ignorance and lack of awareness can create severe IoT security risks. The target of the attack was industrial programmable logic controllers (PLCs), which function similar to IoT devices. The attack happened after a worker plugged a USB flash drive into one of the plant’s computers, causing physical damage to around 1,000 centrifuges. It’s often a doddle to trick a human to gain access to sensitive information and this IoT risk should not be overlooked in social engineering attacks.
Ransomware can Hijack IoT Devices
Ransomware is an evolving IoT attack which stops access to sensitive files. Although a ransomware attack does not cause any harm to your sensitive files, it can lock down the entire functionality of your device. IoT devices with poor security can become targets of ransomware and may put a user in a situation where a hacker asks them to pay a ransom to start their car or unlock their house or for the decryption key to unlock their sensitive files. Just eight days before Trump inauguration speech, cybercriminals attacked police surveillance cameras with ransomware in Washington DC. The ransomware attack infected 70% of the CCTVs and the police couldn’t record for several days. IoT devices like wearables, healthcare gadgets, smart homes, and other smart devices will be at risk of ransomware attacks if there’s cutting corners in security.
Espionage & Eavesdropping
Some IoT devices give unnecessary access to others and put your sensitive information at risk. The interactive IoT doll is a good example which gave access to the toy’s microphone and speaker to anyone within the 25-30 meter radius. It was banned and labeled as an espionage device in Germany. Many IoT devices like health equipment, smart toys, wearables, etc. record user information and hackers can get access to sensitive information if your device behaves like an espionage. Some countries have already started banning IoT devices with security issues.
The security risks discussed above show how IoT devices are at more risk than other computing devices. Whether it’s IoT software app development or IoT hardware manufacturing, strong security protocols should be followed at all levels to avoid hack attacks.
Logic Simplified offers IoT app development services and keeps security as a top priority. Our IoT app development company builds secure IoT solutions for platforms like Amazon Web Services IoT, Microsoft Azure IoT, Google Cloud IoT, openHAB, IBM Bluemix IoT and more. We are experts in programming languages, development frameworks, communication protocols, sensor technology and 3 party APIs for IoT development. For any query related to IoT development, please write to us at enquiry@logicsimplified.com.
 Get a Quote
Get a Quote